The Sign-ins activity report provides data regarding sign-in activity for your tenant, including users and other security or service principals. The report includes information regarding the user, the status of the request, the resource name used for the sign-in, whether multi-factor authentication or conditional access was required, as well as regional location and IP address information:
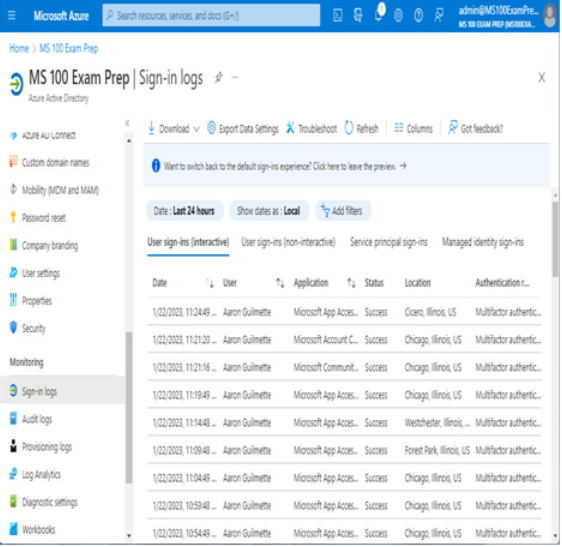
Figure 2.17 – Sign-in logs
Selecting an individual sign-in event brings up advanced details. Each tab contains additional information regarding the sign-in event. See Figure 2.18:
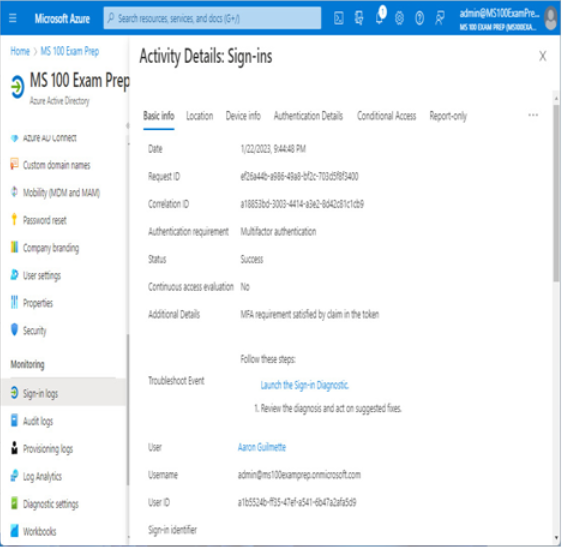
Figure 2.18 – Sign-in activity details
Sign-ins logs are available to all subscriptions, though programmatic access to this data via the Graph API requires either Azure AD Premium P1 or P2.
Provisioning logs
The provisioning logs show data regarding users being provisioned into Azure AD from connected applications or to connected applications from Azure AD provisioning workflows.
To view the provisioning logs, a user must be granted one of the following roles:
- Reports Reader
- Security Reader
- Security Operator
- Security Administrator
- Application Administrator
- Cloud Application Administrator
- Global Administrator
Objects created manually through the Azure AD portal, PowerShell, or Microsoft 365 admin center do not appear here, nor do objects synchronized via Azure AD Connect.
Azure Monitor and Log Analytics
Azure Monitor provides a single, unified hub for diagnostic and monitoring data in Azure and connected applications. The easiest way to start reviewing the logs is to select the Log Analytics link under the Monitoring section in Azure Active Directory, as shown in Figure 2.19:
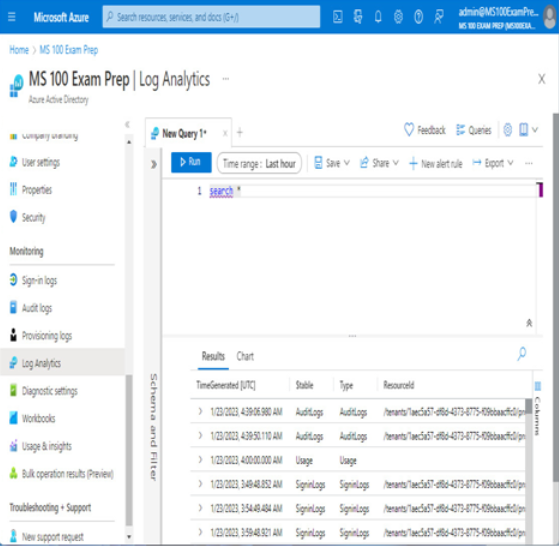
Figure 2.19 – Accessing Log Analytics from the Monitoring section of Azure AD
Log analytics data can be searched using built-in queries or by specifying your own searches in the Query window.
For example, you can select built-in queries to begin querying data immediately. Figure 2.20 shows a query for the SigninLogs table, summarizing sign-ins by country:
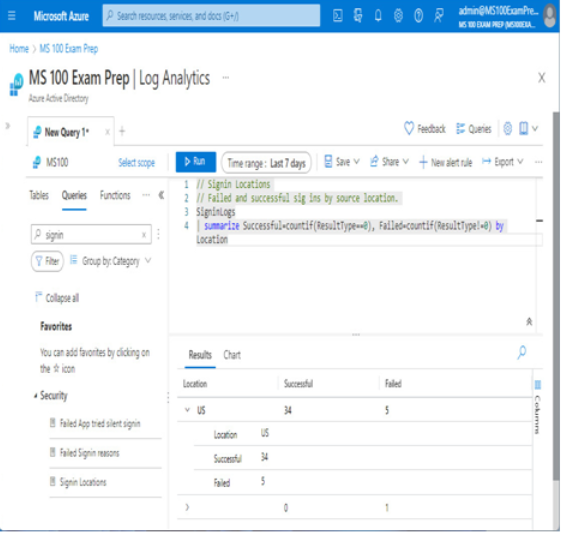
Figure 2.20 – Querying Log Analytics
Deep-dive into Kusto Query Language
Kusto Query Language (KQL) is used to search for and sort through data in Log Analytics. It is an incredibly powerful language but takes some time to learn. KQL is used in Log Analytics, Azure Monitor, and Azure Sentinel. If you want to start learning KQL, you can work through the Log Analytics tutorial at https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-tutorial.
Reviewing usage metrics
For your organization to get the most benefit from a Microsoft 365 investment, users must adopt the available services and features. You can monitor end user adoption and consumption metrics through a variety of tools, including Microsoft 365 Usage Metrics, Viva Insights (formerly known as Workplace Analytics), and Adoption Score (formerly known as Productivity Score).