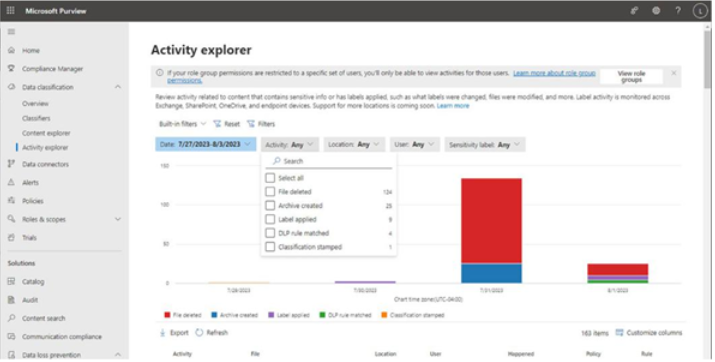
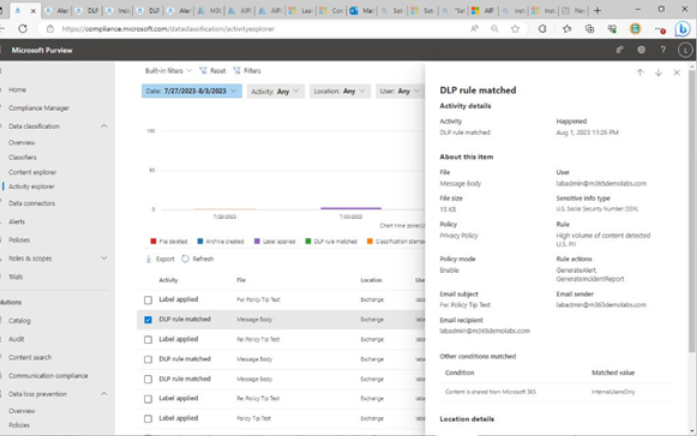
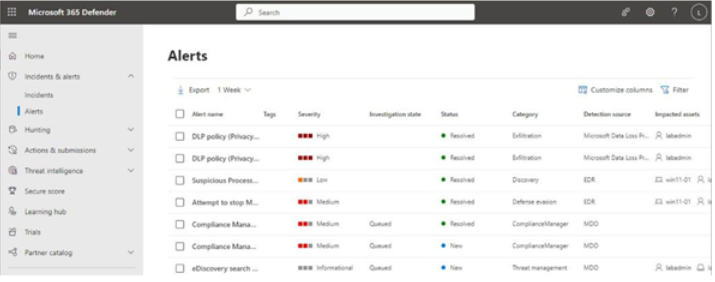
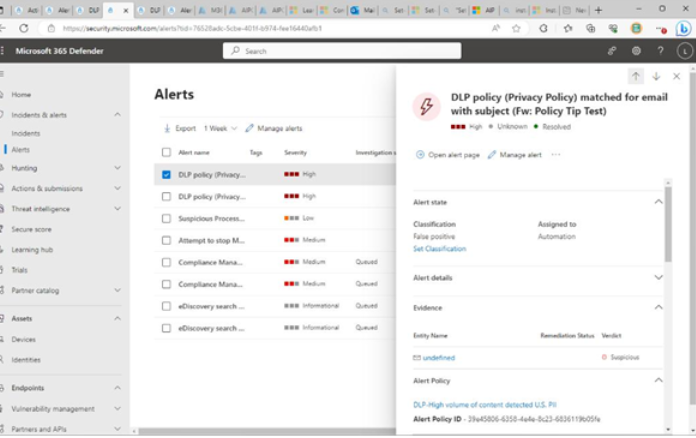
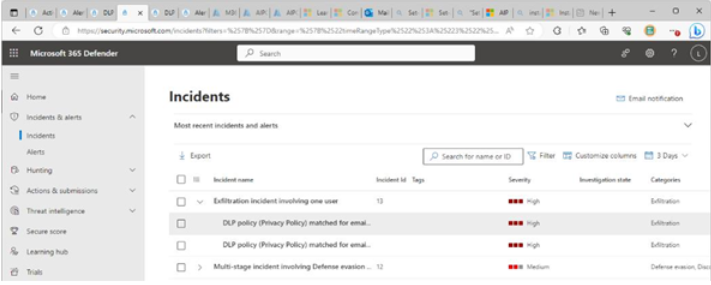
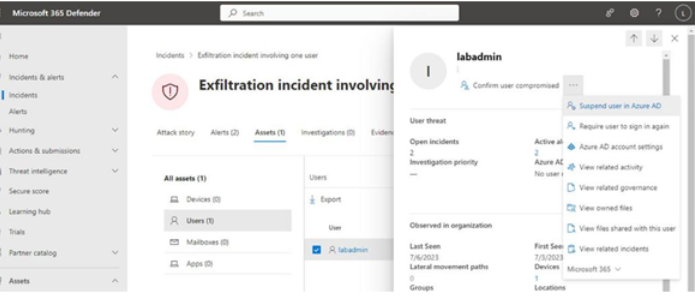
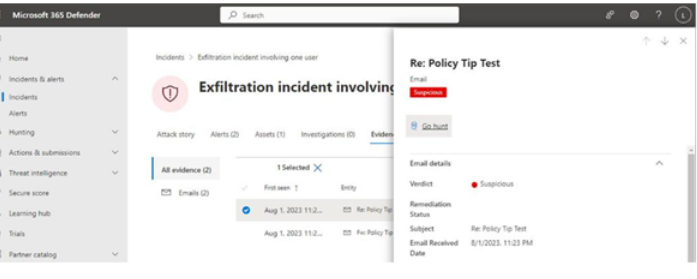
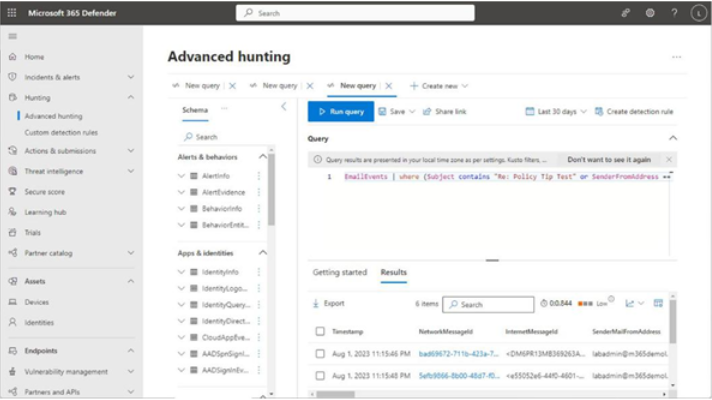
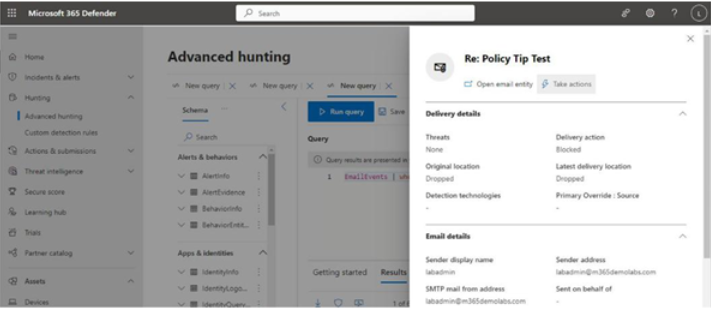
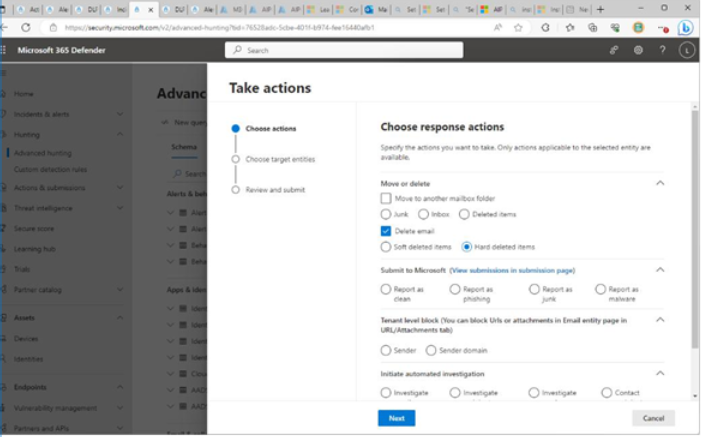
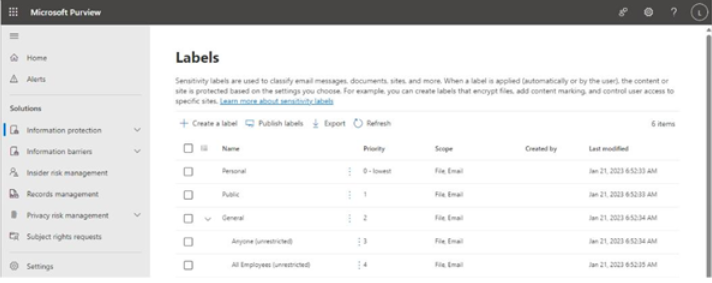
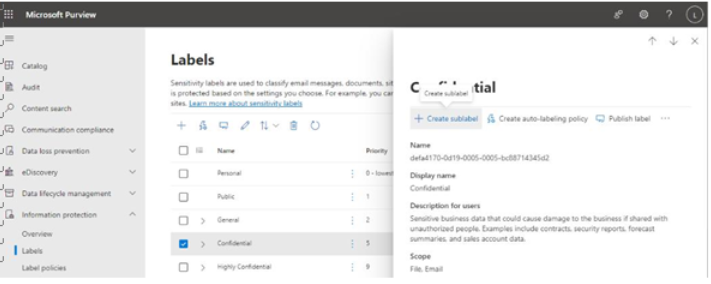
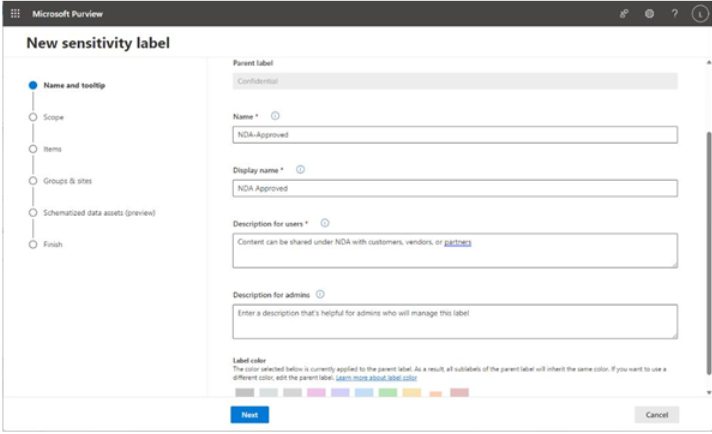
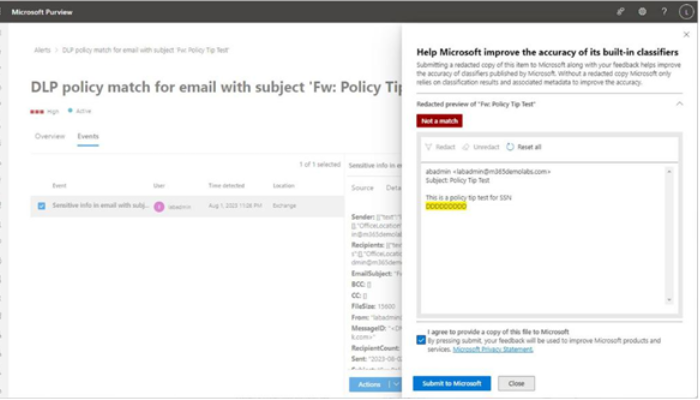
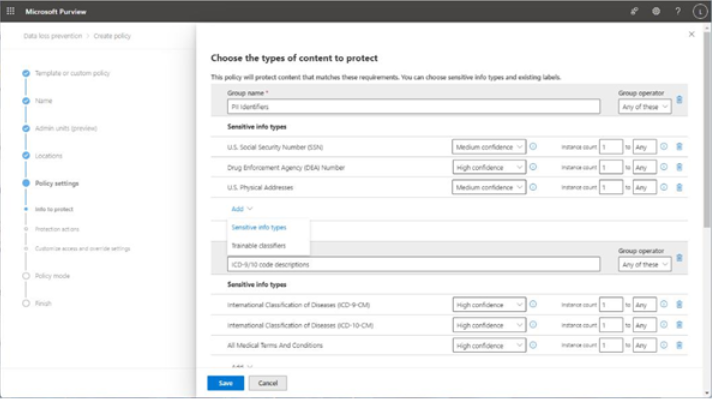
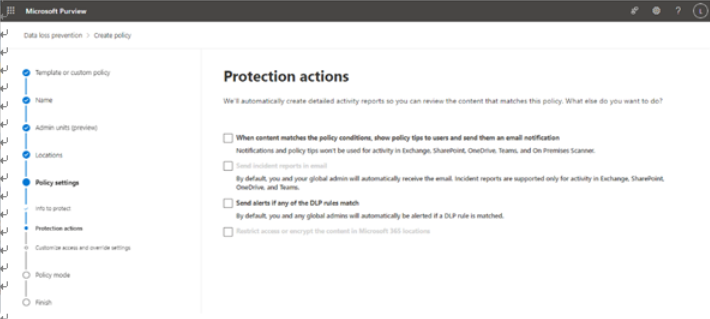
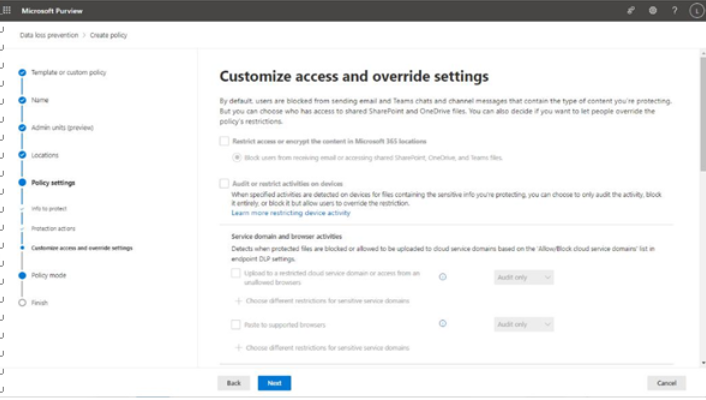
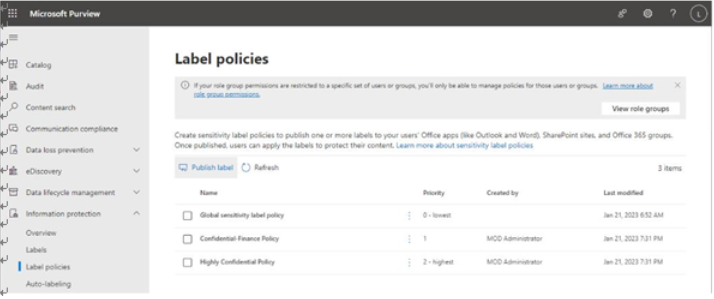
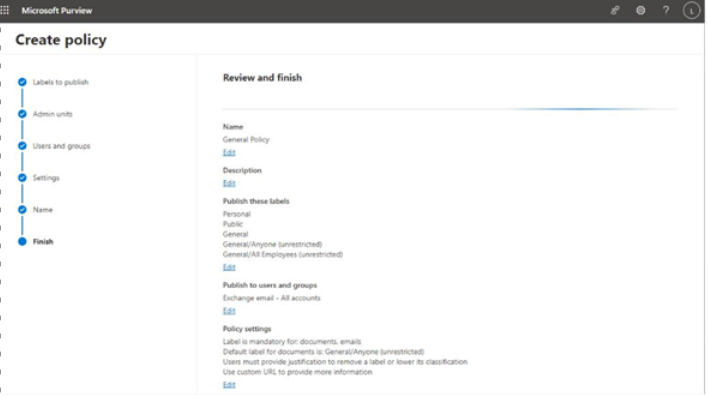
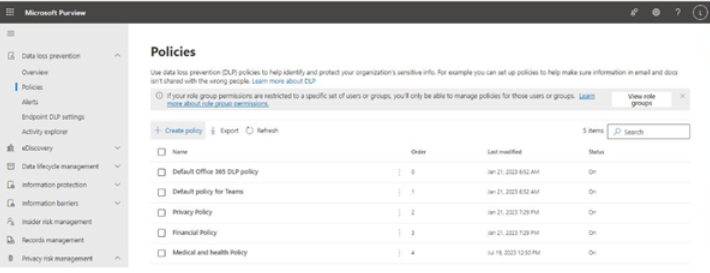
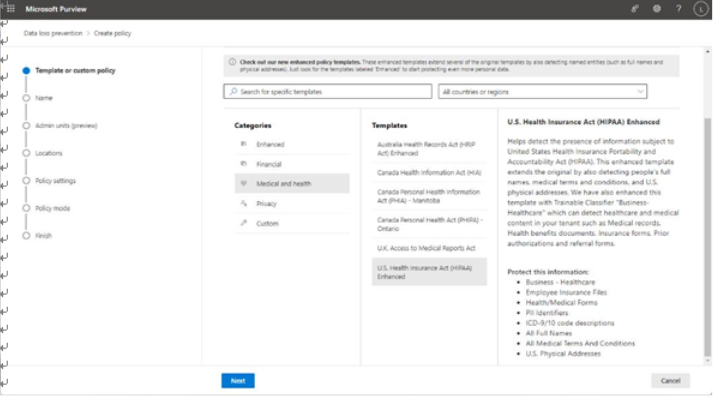
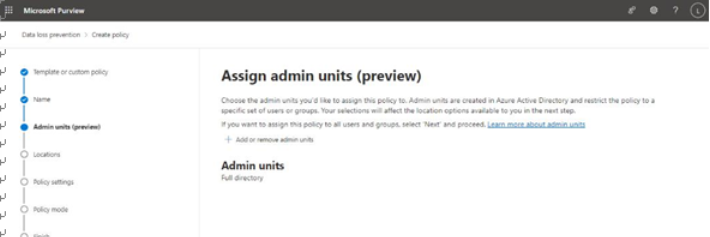
Viva Insights Teamwork habits, part of the premium Viva Insights experience, allows managers to gain additional recommendations for managing people. Teamwork habits helps managers identify regular after-hours work, meeting overload conditions, and a lack of dedicated focus time.
Managers can set up their teams by manually adding users, though they can use the suggested list if the manager property has been configured in Active Directory or Azure Active Directory:
Figure 2.25 – Confirming team members
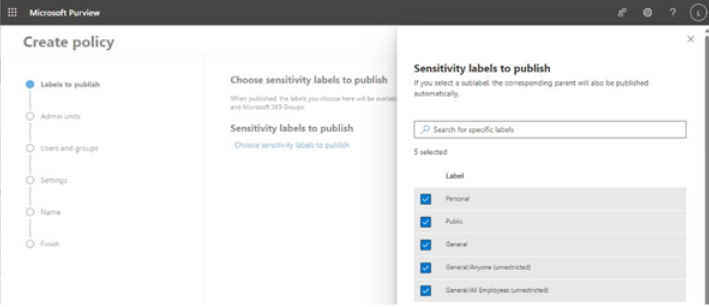
Three additional core features of Teamwork habits are as follows:
- Scheduling recurring 1:1 time with managed employees
- Gathering quiet hours impact to determine how work habits impact employees outside of their configured working hours
- Shared plans for no-meeting days and shared focus times
Organizations that have the Teamwork habits tools available can improve their employees’ well-being and work-life balance. The Teamwork habits feature requires a separate Microsoft Viva Insights license.
Organization trends
The Organization trends tab shows business leader and manager insights to help understand how to effectively manage your teams, such as identifying work patterns:
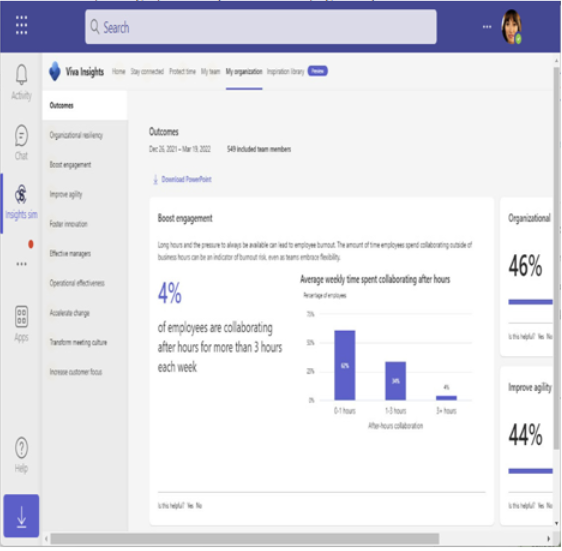
Figure 2.26 – Organization trends
Organization trend data is privacy-oriented, requiring a minimum of 10 people (including the manager) to be in the management chain, either directly or indirectly. In addition, access to organization trends requires granting access to manager insights through the Viva setup.
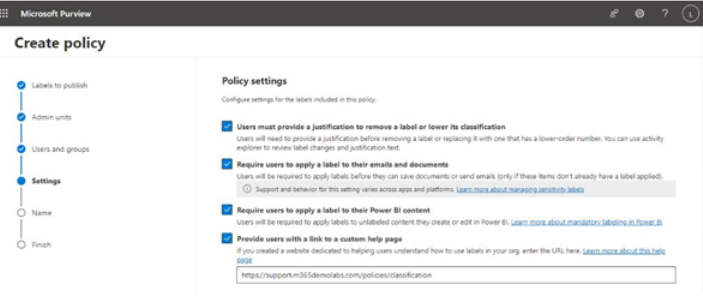
Advanced insights
Microsoft Viva Advanced Insights is a reporting tool that provides research-based behavioral insights into organizational work patterns, such as hybrid work, work-life balance, and employee well-being.
The Advanced Insights reporting tool comes with several built-in templates and analysis tools to help organizations understand everything, from meeting effectiveness to employee performance trends correlated to manager 1:1 meetings:
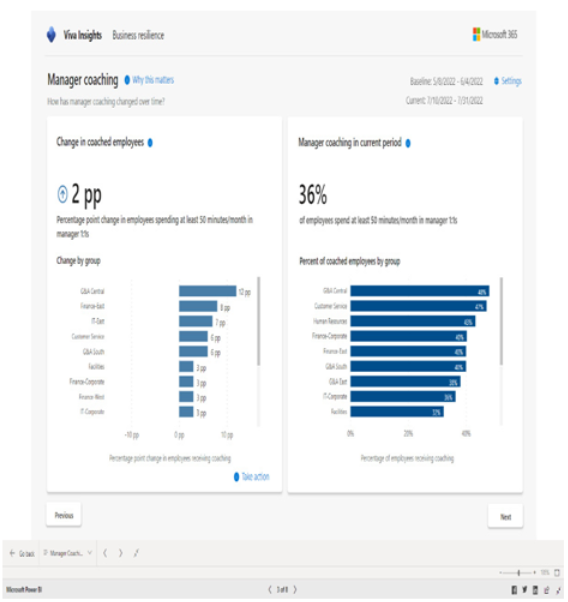
Figure 2.27 – Viva Insights manager coaching report
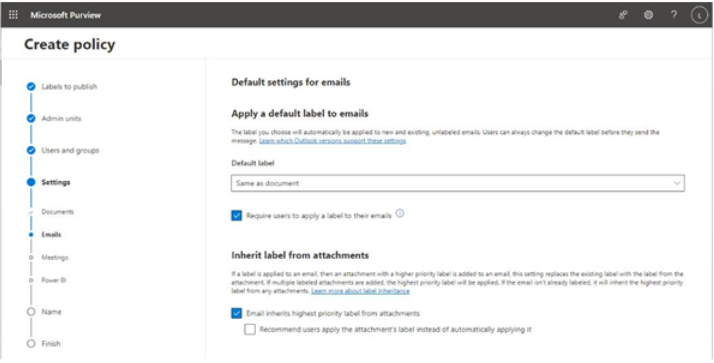
With large organizational changes such as hybrid and remote work scenarios, it can be important to understand how those work patterns affect performance, including interesting data points such as how much time is spent during meetings multitasking, or how much work is getting done outside normal business hours:
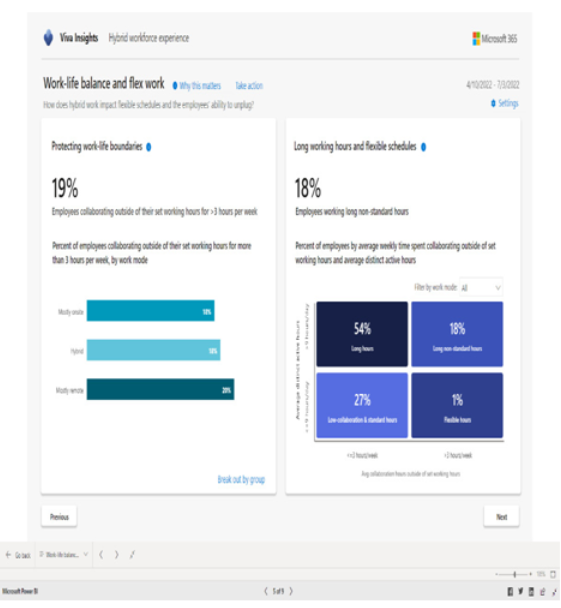
Figure 2.28 – Advanced insights working hours details
The Advanced Insights Power BI report templates provide an analysis of employee engagement and work patterns. Here are the reports:
- Business resilience: Overall business report highlighting performance and employee well-being
- Hybrid workforce experience: This report highlights how different work modes (onsite, hybrid, and remote) affect workers
- Manager effectiveness: This report provides insight into patterns for people managers
- Meeting effectiveness: This report captures and displays information on meeting statistics such as how many meetings happen at short notice or how much multitasking occurs during meetings
- Ways of working: This data helps answer questions such as, “Are employees receiving enough 1:1 coaching time?” and “Who generates the most work by organizing meetings?”
- Wellbeing – balance and flexibility: This reporting data is used to identify whether employees have enough time to focus on core priorities and balance that with breaks and time away from work
For more information on the advanced insights templates and their reporting capabilities, see https://learn.microsoft.com/en-us/viva/insights/advanced/analyst/templates/introduction-to-templates.