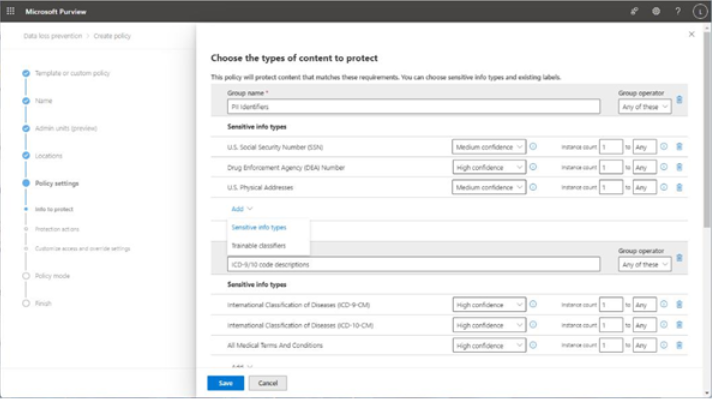
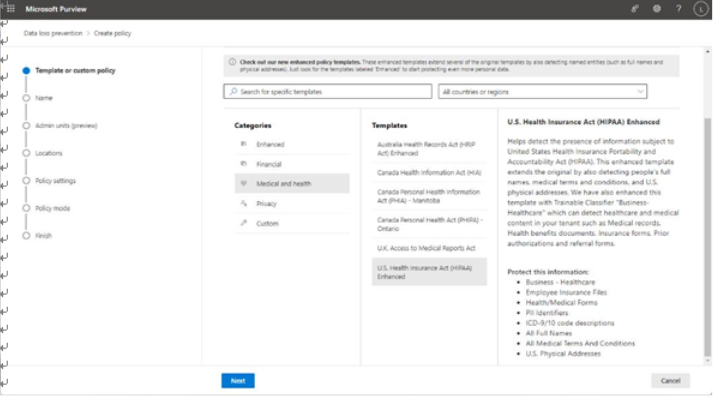
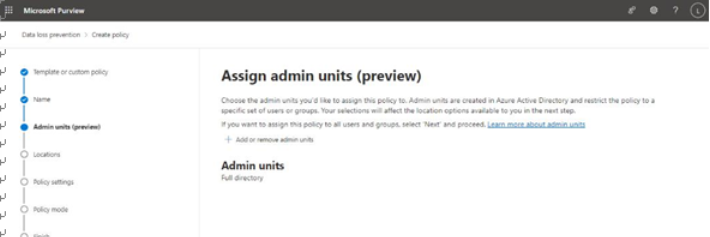
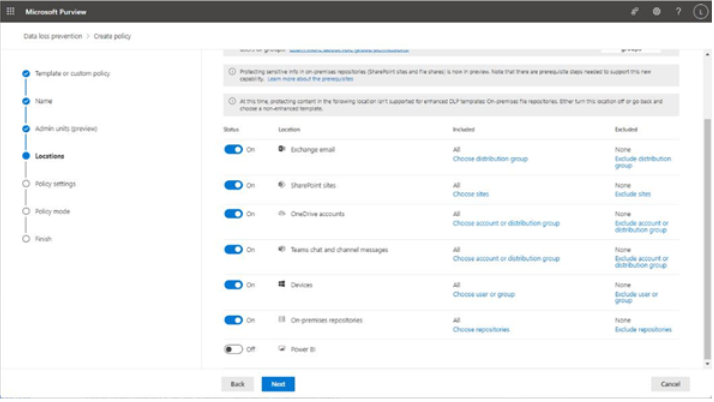
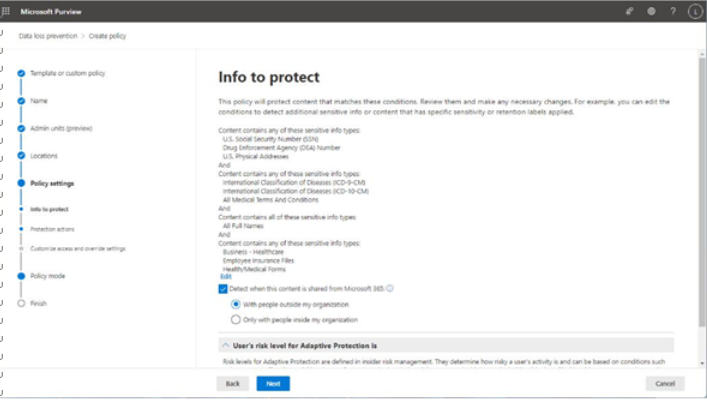
The easiest place to view DLP alerts is on the Alerts dashboard, located in the Microsoft Purview compliance portal under Data loss prevention. Figure 11.26 depicts an alert that was generated based on a DLP policy using a template to detect personal information, such as social security numbers:
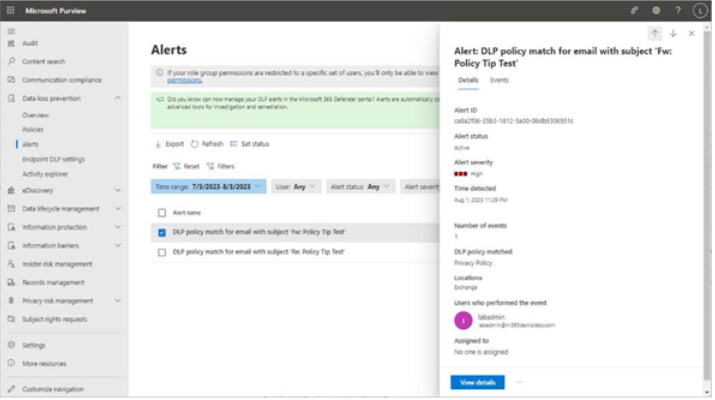
Figure 11.26 – Viewing a DLP alert
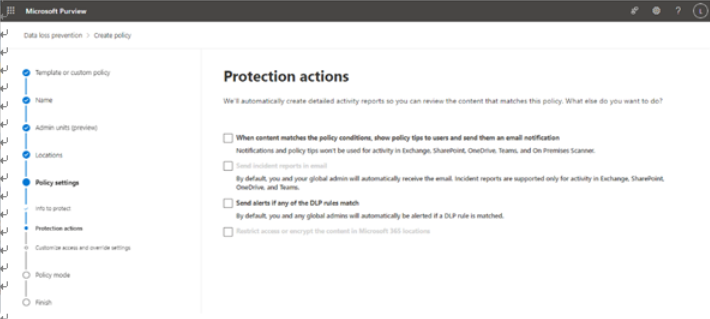
You can view more details about the alert by selecting the View details button at the bottom of the flyout. The detail view of an alert displays a number of fields on the Overview tab, such as a plain-text summary of the event, actor details (who did it), the policy that was matched, and the corresponding rule and sensitive information types inside the rule, basic information about the alert, such as the severity and time detected, as well as other alerts related to the user or actor. See Figure 11.27:
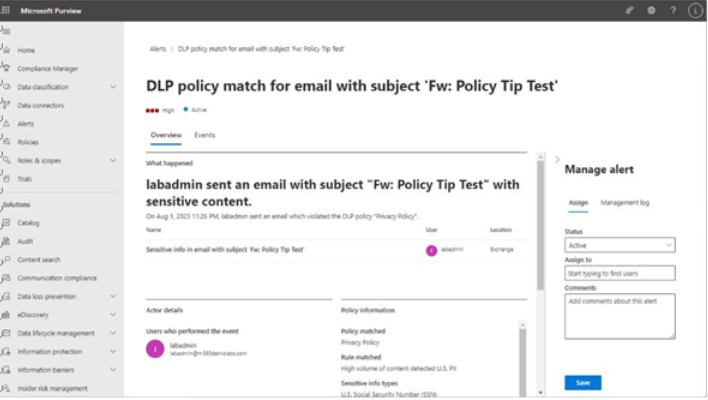
Figure 11.27 – Alert detail page
On the Manage alert pane, you can update the status of a particular DLP event. When first detected, the alert is set to Active. You can select additional statuses such as Investigating, Dismissed, or
Resolved. Updating the status in the Alerts dashboard to Investigating will set the corresponding event’s status to In Progress in the Microsoft 365 Defender incident. Updating the alert status to either Dismissed or Resolved will set the corresponding event’s status to Resolved in the Microsoft 365 Defender incident.
Note
While setting the alert’s status to Dismissed or Resolved in the compliance portal will update the alert’s status to Resolved in the Microsoft 365 Defender portal, setting an alert’s status to Dismissed will also result in the classification in Microsoft 365 Defender being set toFalse positive.
Selecting the Events tab on the alert detail page will show much of the same information but arranged in a different order. New data presented, however, includes additional information about actors and intended recipients, classifiers or sensitive info types used to match content, and the context of the data inside the file or message that triggered the alert.
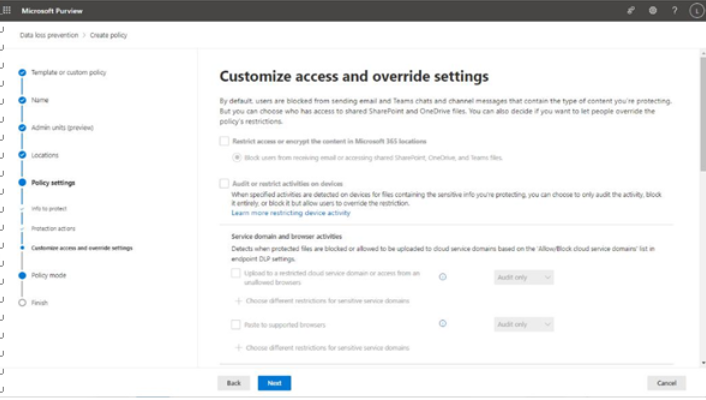
If you’ve configured a policy to allow user override and the user exercised that option, you can see that data here as well, along with any business justification text that was submitted, as shown in Figure 11.28:
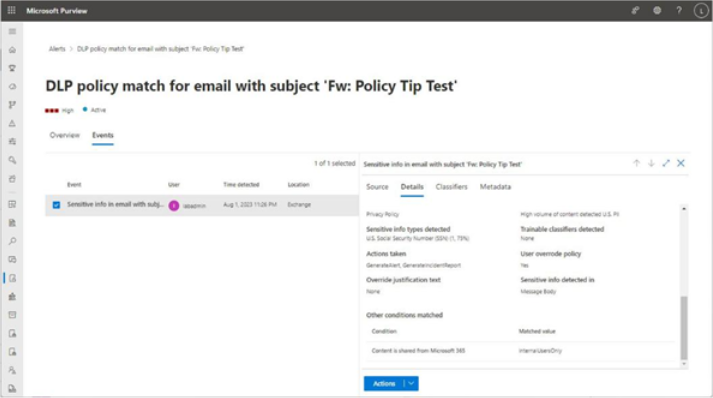
Figure 11.28 – Event detail view of an alert
If you have configured encryption for the items matching the DLP policy, the Source tab may display a warning that the content is encrypted, prompting you to download the file or message in order to view it. However, the Classifiers tab will show examples of content that matches the policy rules. It’s important to only delegate compliance-related roles to individuals your organization trusts to address issues arising from viewing potentially sensitive information. The Metadata tab will show the underlying data for the policy match conditions and will also include the matched content values.
On the Actions tab for an event, you can choose to download the item or mark it as Not a match.
If you select Not a match, you have the option of submitting a redacted sample to Microsoft to help improve the accuracy of scan detections. See Figure 11.29:
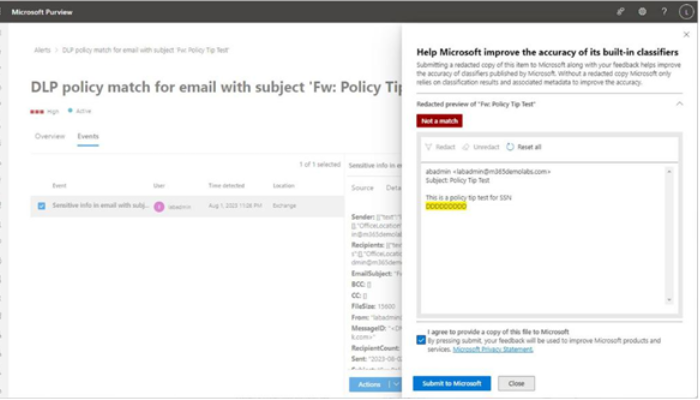
Figure 11.29 – Submitting a redacted false positive sample to Microsoft
While this section specifically covers the DLP view of the Alerts dashboard, the broader compliance portal Alerts view is the same but also includes compliance events from sources besides DLP. The management tasks, item details, and interfaces are the same.